Certificate
Setting up the Certificate
Enhance the Makefile in the infrastructure git project with the following content:
.PHONY: app-staging-certificates
app-staging-certificates: guard-STAGE
aws cloudformation deploy \
--no-fail-on-empty-changeset \
--template-file cloudformation/certificates.yml \
--stack-name certificates-$(STAGE) \
--parameter-overrides Stage=$(STAGE) \
--region $(AWS_REGION)
Create a new cloudformation template in app-staging/certificates.yml and define the certificates in there:
---
AWSTemplateFormatVersion: 2010-09-09
Description: Certificates
Parameters:
Stage:
Type: String
Mappings:
CertificateDomains:
dev:
Domain: app.dev.aws.myorg.com
prod:
Domain: app.prod.aws.myorg.com
Resources:
Certificate:
Type: AWS::CertificateManager::Certificate
Properties:
DomainName:
'Fn::FindInMap': [ "CertificateDomains", !Ref Stage, "Domain" ]
SubjectAlternativeNames:
- 'Fn::Sub': ['*.${Domain}', { 'Domain': {'Fn::FindInMap': [ "CertificateDomains", !Ref Stage, "Domain" ]}}]
ValidationMethod: DNS
Outputs:
CertificateArn:
Description: 'Certificate ARN.'
Value: !Ref Certificate
Export:
Name: !Sub '${AWS::StackName}-CertificateArn'
Create the Cloudformation stack with the following command in the app-staging AWS account
AWS_PROFILE=myorg-app-staging make app-staging-certificates STAGE=dev
During the stack creation Cloudformation waits for the DNS validation to finish.
That’s why the command blocks and does not finish.
Leave this running in the terminal and go to the AWS Console.
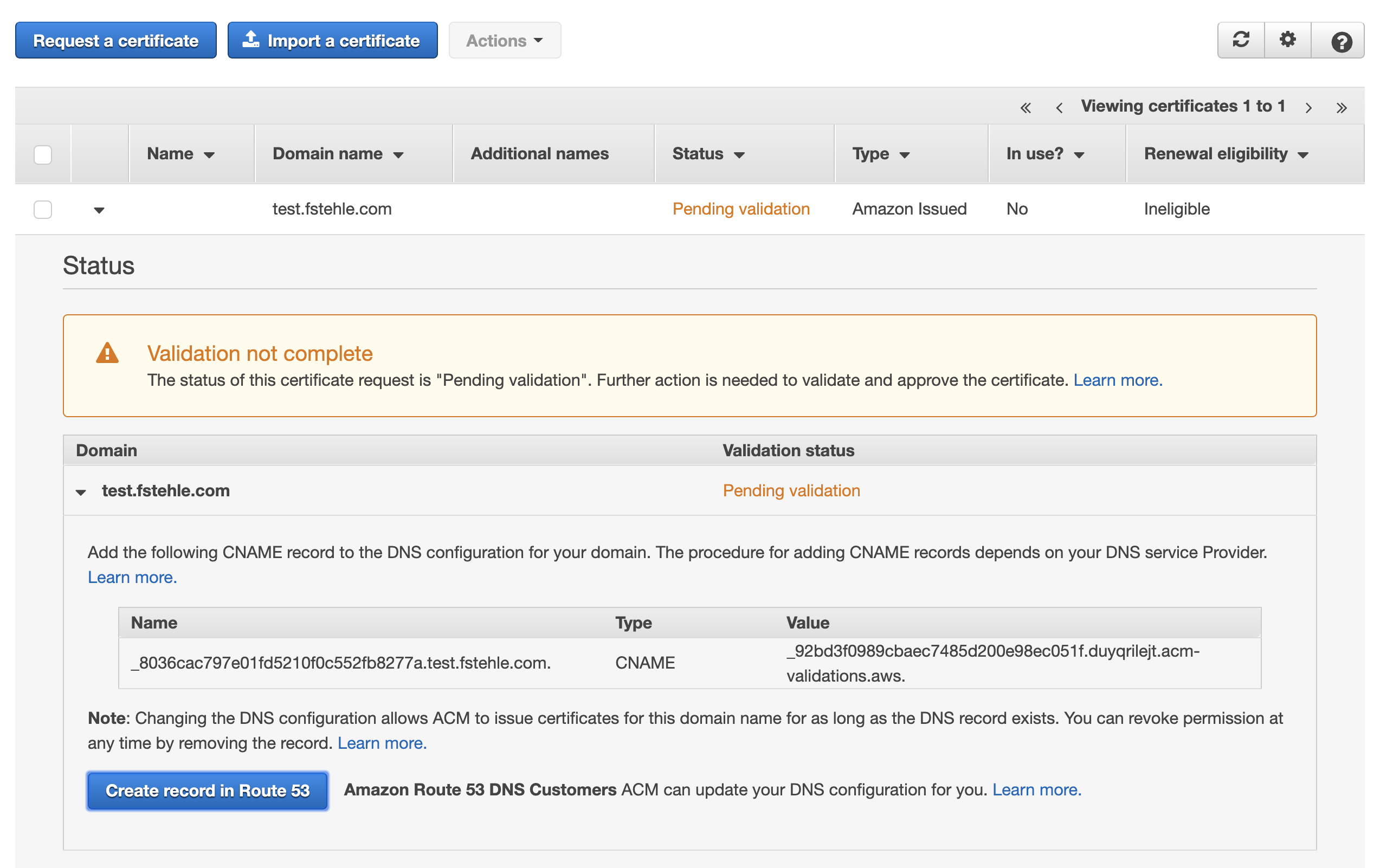
Open the Certificate Manager and scroll to your certificate. This should have a Validation status of Pending validation.
Expand the certificate by clicking on the arrow. Expand the domain as well.
You should see a button Create record in Route53.
Click this button to create the records.
The validation should succeed after some minutes and the Cloudformation stack should succeed.